Common types of attacks
In this tutorial we will learn some popular types of attacks which are introduced in the SCOR syllabus.
The first one is Code Injection Attacks. There are two popular types of Code Injection Attacks: SQL Injection and Cross Site Scripting.
SQL injection usually occurs when you ask a user for input, like their username/userid, but the user gives (“injects”) you an SQL statement that you will unknowingly run on your database.
Look at the following example, the administrators (or programmers) of the website directly created a SELECT statement by adding a variable from the user input (txtUserId) to a select string without any safety checks. The variable “UserId’ was fetched from user input (getRequestString):
| txtUserId = getRequestString(“UserId”); txtSQL = “SELECT * FROM Users WHERE UserId = ” + txtUserId; |
If user enter something like this: “100 OR 1=1” then the SQL statement will look like this:
| SELECT * FROM Users WHERE UserId = 100 OR 1=1; |
The SQL above is valid and will return ALL rows from the “Users” table, since OR 1=1 is always TRUE. A hacker might get access to all the user names and passwords in this database.
Cross site scripting attack (also known as XSS) occurs when a web application gathers malicious data from a user. The data is usually gathered in the form of a hyperlink which contains malicious content within it. The user will most likely click on this link from another website, instant message, or simply just reading a web board or email message.
Usually the attacker will encode the malicious portion of the link to the site in HEX (or other encoding methods) so the request is less suspicious looking to the user when clicked on.
For example the code below is written in hex:
<a href=javascript:alert('XSS')>Click Here</a>
is equivalent to:
<a href=javascript:alert('XSS')>Click Here</a>
Note: In the format “&#xhhhh“, hhhh is the code point in hexadecimal form.
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. Phishing is a form of social engineering and it is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine.

In deceptive phishing, fraudsters impersonate a legitimate company in an attempt to steal people’s personal data or login credentials. Those emails frequently use threats and a sense of urgency to scare users into doing what the attackers want.
Spear phishing is carefully designed to get a single recipient to respond. Criminals select an individual target within an organization, using social media and other public information – and craft a fake email tailored for that person.
The directory traversal/path traversal attack (also known as dot dot slash attack) is an HTTP exploit that allows an attacker to access restricted files, directories and commands that reside outside the web server’s root directory.
A Denial-of-Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a network, service, website, or online resource by overwhelming it with a flood of illegitimate or excessive traffic. The goal of a DoS attack is to make the targeted system or network unavailable to its intended users, effectively denying them access to the services it provides.
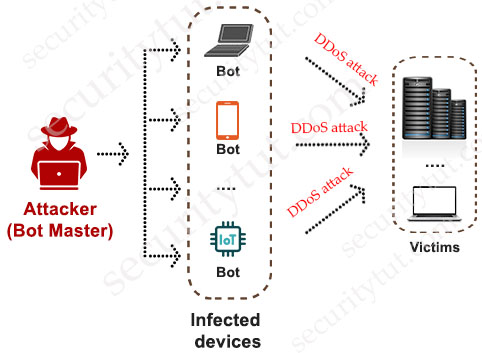
Common types of DoS Attacks
+ Buffer overflow: A buffer overflow attack is a type of security vulnerability that occurs when a program or process attempts to write more data into a buffer (a temporary storage area in memory) than it can hold. Buffer overflow is a vulnerability in low level codes like C and C++. This can lead to the excess data overflowing into adjacent memory locations, potentially overwriting important data, altering program behavior, make data corrupt, steal some private information or run attacker’s code or even causing the program to crash.
+ Smurf Attack: A Smurf attack is a type of distributed denial-of-service (DDoS) attack that exploits the characteristics of Internet Control Message Protocol (ICMP) and the concept of broadcast addressing to overwhelm a target network or system. It was named after the fictional characters “Smurfs,” who were known for their habit of working together in large groups. In a Smurf attack, the attacker sends a large number of ICMP echo request packets (also known as “ping” requests) to a network’s broadcast address, using the source IP address of the victim’s target. When these ping requests are broadcasted to the entire network, all devices on that network respond with ICMP echo replies. Since the source address of the ping requests is spoofed to be the victim’s address, all the replies are directed to the victim’s IP address, overwhelming its network and potentially causing a denial of service.
+ Ping flood: a type of DoS attack that involves sending a large number of ICMP echo request packets (commonly known as “ping” requests) to a target victim. The goal of a ping flood attack is to overwhelm the target’s network resources or system, causing it to become slow, unresponsive, or even crash.
+ Ping of Death (PoD): a type of DoS attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
A correctly-formed ping packet is typically 56 bytes in size, or 64 bytes when the ICMP header is considered, and 84 including Internet Protocol version 4 header. However, any IPv4 packet (including pings) may be as large as 65,535 bytes. Some computer systems were never designed to properly handle a ping packet larger than the maximum packet size because it violates the Internet Protocol documented
Like other large but well-formed packets, a ping of death is fragmented into groups of 8 octets before transmission. However, when the target computer reassembles the malformed packet, a buffer overflow can occur, causing a system crash and potentially allowing the injection of malicious code.
+ SYN flood attack is a type of network-based denial-of-service (DoS) attack that targets the three-way handshake process of the Transmission Control Protocol (TCP), a fundamental protocol used for establishing connections between devices over the Internet. The goal of a SYN flood attack is to overwhelm a target system’s ability to establish new TCP connections, effectively rendering it slow, unresponsive, or even inoperable.
The main steps of a SYN flood attack are as follows:
1. The attacker sends a flood of SYN packets to the target server.
2. The target server responds with SYN-ACK packets to each incoming SYN packet.
3. The attacker does not send the expected ACK packets, leaving the server with half-open connections in a pending state.
4. As the number of half-open connections increases, the server’s resources, such as memory and connection slots, become exhausted.
5. Legitimate users may experience difficulty connecting to the server, or the server may become unresponsive.



Hey people!!!!!
Good mood and good luck to everyone!!!!!