Cisco Umbrella
|
Cisco Umbrella Quick Summary Cisco Umbrella protects users from accessing malicious domains by proactively analyzing and blocking unsafe destinations – before a connection is ever made. Thus it can protect from phishing attacks by blocking suspicious domains when users click on the given links that an attacker sent. When Umbrella receives a DNS request, it uses intelligence to determine if the request is safe, malicious or risky — meaning the domain contains both malicious and legitimate content. Safe and malicious requests are routed as usual or blocked, respectively. Risky requests are routed to our cloud-based proxy for deeper inspection. The Umbrella proxy uses Cisco Talos web reputation and other third-party feeds to determine if a URL is malicious. Cisco Umbrella roaming protects your employees even when they are off the VPN. Cisco Umbrella has the following security categories: + C2 Callbacks – Prevent compromised devices from communicating with hackers’ command and control servers
|
Question 1
Question 2
Explanation
SSL Decryption is an important part of the Umbrella Intelligent Proxy. he feature allows the Intelligent Proxy to go beyond simply inspecting normal URLs and actually proxy and inspect traffic that’s sent over HTTPS. The SSL Decryption feature does require the root certificate be installed.
Reference: https://support.umbrella.com/hc/en-us/articles/115004564126-SSL-Decryption-in-the-Intelligent-Proxy
Question 3
Explanation
The logging of your identities’ activities is set per-policy when you first create a policy. By default, logging is on and set to log all requests an identity makes to reach destinations. At any time after you create a policy, you can change what level of identity activity Umbrella logs.
From the Policy wizard, log settings are:
Log All Requests—For full logging, whether for content, security or otherwise
Log Only Security Events—For security logging only, which gives your users more privacy—a good setting for people with the roaming client installed on personal devices
Don’t Log Any Requests—Disables all logging. If you select this option, most reporting for identities with this policy will not be helpful as nothing is logged to report on.
Reference: https://docs.umbrella.com/deployment-umbrella/docs/log-management
Question 4
Explanation
The Cisco Umbrella Multi-Org console has the ability to upload, store, and archive traffic activity logs from your organizations’ Umbrella dashboards to the cloud through Amazon S3. CSV formatted Umbrella logs are compressed (gzip) and uploaded every ten minutes so that there’s a minimum of delay between traffic from the organization’s Umbrella dashboard being logged and then being available to download from an S3 bucket.
By having your organizations’ logs uploaded to an S3 bucket, you can then download logs automatically to keep in perpetuity in backup storage.
Reference: https://docs.umbrella.com/deployment-umbrella/docs/manage-logs
Question 5
Question 6
Explanation
When Umbrella receives a DNS request, it uses intelligence to determine if the request is safe, malicious or risky — meaning the domain contains both malicious and legitimate content. Safe and malicious requests are routed as usual or blocked, respectively. Risky requests are routed to our cloud-based proxy for deeper inspection. The Umbrella proxy uses Cisco Talos web reputation and other third-party feeds to determine if a URL is malicious.
Question 7
Explanation
A destination list is a list of internet destinations that can be blocked or allowed based on the administrative preferences for the policies applied to the identities within your organization. A destination is an IP address (IPv4), URL, or fully qualified domain name. You can add a destination list to Umbrella at any time; however, a destination list does not come into use until it is added to a policy.
Reference: https://docs.umbrella.com/deployment-umbrella/docs/working-with-destination-lists
Question 8
Explanation
Cisco Umbrella protects users from accessing malicious domains by proactively analyzing and blocking unsafe destinations – before a connection is ever made. Thus it can protect from phishing attacks by blocking suspicious domains when users click on the given links that an attacker sent. Cisco Umbrella roaming protects your employees even when they are off the VPN.

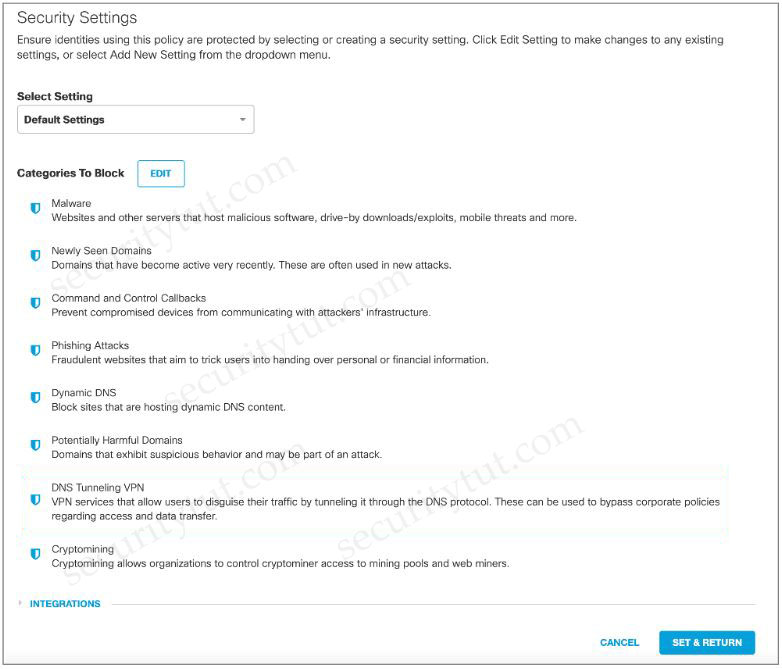


Question 6
There is also a sub-category—Integrations—that’s available for some packages. The Integrations security category consists of domains that have been added to Umbrella through individual integrations.
Umbrella can integrate with:
FireEye
Check Point
Cisco AMP Threat Grid
ThreatConnect
ThreatQ
ZeroFOX
The only Cisco solution here is AMP
Cisco Umbrella uses Cisco Talos, which is not a Cisco Solution and it is not Integration!
https://support.umbrella.com/hc/en-us/articles/231248768-Cisco-Umbrella-Cisco-AMP-Threat-Grid-Cloud-Integration-Setup-Guide
https://docs.umbrella.com/deployment-umbrella/docs/understanding-the-security-categories
The Umbrella proxy uses Cisco Talos web reputation and other third-party feeds to determine if a URL is malicious.
@Securitytut
Question 1
I believe the correct Answer is B , the correct url to test is http://welcome.opendns.com, the other test is enabling Intelligent Proxy, please check the below URL.
https://support.umbrella.com/hc/en-us/articles/230903728-How-To-Successfully-test-to-ensure-you-re-running-Umbrella-correctly